NEWS ALERT: OPSWAT Appoints Distinguished Critical Infrastructure Industry Veterans to Board of Directors - Read Now
File: burn a dmg image in windows. This software was checked for viruses and was found to contain no viruses. Burning a.dmg using Windows, Hello there, I am having some troubles burning a.dmg (Mac image file) onto a disk, using Windows (XP and Vista). I searched and searched. I believe most Windows anti-virus software can scan DMGs, and most Mac anti-virus software just scans for Windows viruses so a Mac user can't pass it on to their friends. Snow Leopard (the latest version of the Mac OS) has built in anti-malware protection (just make sure you're up to date by running Software Update!) so you should be a-okay!
CLOSEXContact UsSolutionsSolutionsCross-Domain SolutionsGovern and secure data or device transfer for your segmented and air-gapped network environments.
 MetaDefender KioskMetaDefender VaultMetaDefender DriveMetaDefender USB FirewallSecure Access
MetaDefender KioskMetaDefender VaultMetaDefender DriveMetaDefender USB FirewallSecure AccessSecure local or remote access to your cloud applications, internal networks and resources.
MetaAccess PlatformMetaAccess SDPCloud Security for Salesforce File Upload SecurityPrevent malicious file uploads that can compromise your networks.
MetaDefender ICAP ServerMetaDefender CoreMetaDefender Core AMIFile Upload Security AssessmentMetaDefender CloudMalware AnalysisAnalyze suspicious files or devices with our platform on-prem or in the cloud.
The majority of malware continues to be initiated via email. OPSWAT Protects Your Organization Against Advanced Email Attacks.
MetaDefender Email Gateway SecurityNetwork Access ControlPrevent risky devices including BYOD and IoT from accessing your networks with full endpoint visibility.
Protect your on-prem or cloud storage services and maintain regulatory compliance.
Join hundreds of security vendors benefiting from OPSWAT’s industry-leading device and data security technologies.
Use our on-demand courses to get trained and certified on cyber security concepts and best practices, critical infrastructure protection, and OPSWAT products and solution. Both introductory and advanced courses are available.
Courses and CertificationsThe OPSWAT Academy consists of subject matter courses designed for the learner to build up their expertise using a phased approach.
For current OPSWAT customers, the Academy also includes advanced training courses for greater ease-of-use efficiency when operating and maintaining all OPSWAT products and services.
Available Certifications
Certified Cyber-security AssociateCertified MetaDefender AssociateCertified MetaAccess AssociateCertified Secure Data Workflow AssociateCritical Infrastructure Protection AssociateCertification RenewalEach discipline certification is awarded for one year upon passing the exams on that discipline's courses in OPSWAT Academy.
In order to maintain active OCIPA Certification, make sure you stay current on all OPSWAT's individual discipline certifications.
OCIPA Certification RenewalTrust no file. Trust no device.PartnersPartnersAccess Control Certification ProgramA Service that verified compatibility and effectiveness of endpoint next-gen antimalware, antimalware and disk encryption products.
Platinum Level ProductsGold Level ProductsAll ProductsTechnology PartnersEnhance threat prevention by integrating OPSWAT technologies. OPSWAT partners with technology leaders offering best-of-breed solutions with the goal of building an ecosystem dedicated to data security and compliance using integrated solutions.
Categories
 Technology Alliance PartnerMalware Sharing ProgramMetaDefender Core Engine SupplierMetaDefender Cloud Engine SupplierChannel Partners
Technology Alliance PartnerMalware Sharing ProgramMetaDefender Core Engine SupplierMetaDefender Cloud Engine SupplierChannel PartnersOur partner program is aimed at providing the most effective and innovative products and tools to help accelerate your business.
Channel Partner ProgramChannel Program ApplicationPartner Portal Channel Partner DirectoryTrust no file. Trust no device.ServicesServicesProfessional ServicesSecurity AssessmentsSolution ImplementationsCustom IntegrationsOngoing MaintenanceManaged ServicesSupportThe OPSWAT’s support team can provide you 24x7x365 coverage via phone, chat, or cases that you log with you.
Support PlansSupport Contact InfoOPSWAT Portal Create a Case Knowledge Center Online Documentation Training ServicesTake advantage of our instructor led training (ILT) courses or onsite “walk the floor” coaching to augment and expand on the training received through OPSWAT Academy courses.
Training Courses“Floor Walking” Q&AOPSWAT AcademyUse our on-demand courses to get trained and certified on cyber security concepts and best practices, critical infrastructure protection, and OPSWAT products and solution. Both introductory and advanced courses are available.
About AcademySignup / Log inRenewCommunityJoin the conversation, and learn from others in our Community Forum. Our customers drive us forward, contribute product ideas, and get their questions answered.
Community ForumsJoin the CommunitySign in to ForumsTrust no file. Trust no device.CompanyCompanyAboutOPSWAT provides Critical Infrastructure Protection solutions to protect against cyberattacks.
Management TeamContact UsCompliance and CertificationsCustomersOver 1,000 customers worldwide trust OPSWAT to protect their digital assets and keep their data flows secure.
CustomersCase StudiesCareersOPSWAT teams are filled with smart, curious and innovative people who are passionate about keeping the world safer. Join us, unleash your talent and help protect worldwide Critical Infrastructure.
Build your Career with OPSWATOpen PositionsEvents and WebinarsLearn how OPSWAT cybersecurity solutions can protect your organization against cyberattacks by visiting with us at conferences and attending webinars
EventsWebinarsNews & Media CenterBlogPress ReleasesBrand ResourcesOPSWAT in the NewsResourcesResources to learn about critical infrastructure protection and OPSWAT products.
Trust no device.EN
Originally Published February 17, 2014.
Video files are not typically thought of as potentially malicious or infected file types, but it is possiblefor malware to be embedded in or disguised as a video file. Due to this common misconception, audio andvideo files are intriguing threat vectors for malware writers.
Why the Concern for Video Files?
- Media players are frequently used software, users tend to use them for an extended period of time leaving themopen during other tasks, and frequently switch media streams.
- Many vulnerabilities are found in media players. NIST [1] shows more than 1,200 vulnerabilities from 2000 to2014 [2]. In early 2020, NIST recorded a new high-severity vulnerability, CVE-2020-0002, in Android MediaFramework.
- Attractive video content and high-speed internet leads users to download and share without paying attention, and as these files are perceived as relatively harmless, users are likely to play files given to them.
- The file formats involved are binary streams and tend to be reasonably complex. Much parsing is required tomanipulate them, and playback calculations can easily result in integer bugs.
- The file is usually large; users are likely to skip scanning solutions to avoid performance impact.
- They are perceived as relatively harmless - users are likely to play files given to them.
- There are a wide variety of different audio players and many of different codecs and audio file plugins, allwritten by generally non-security-focused people.
- Users download videos from many unreliable sources, and the videos run with fairly high privilege and priority.For instance, in Windows Vista, a low-privileged Internet Explorer instance can launch content in ahigher-privileged Windows Media Player.
- Videos are frequently invoked without the user's explicit acknowledgement (i.e. embedded in a web page) [3].
Typical Vulnerability Vectors
Fuzzing the media player by a modified video file
Fuzzing is a generic method to force a program to behave unexpectedly by providing invalid, unexpected, or randomdata to the inputs.
Fuzzing is designed to find deep bugs and is used by developers to ensure the robustness of code, however, adeveloper's best tool can be used to exploit the user as well. For media players, which are supposedly 'formatstrict,' a corrupted real video file can expose many bugs, most caused by dereferencing null pointers. This resultsin inappropriate memory access, which offers the possibility of writing to memory something that is not intended tobe written [4]. Fortunately, fuzzing media players requires in-depth knowledge of the file format or else thecorrupted file, will simply be ignored by the player.
Embedding hyperlinks in a video file
A more direct method is obtained by embedding a URL into modern media files.
For example, Microsoft Advanced System Format (ASF) allows for simple script commands to be executed. In this case,'URLANDEXIT' is placed at a specific address and following any URL. When this code executes, the user is directed todownload an executable file, often disguised as a codec and prompting the user to download in order to play themedia.
MetaDefender Cloud, OPSWAT's anti-malware multiscanning tool, has an example of one such file:https://metadefender.opswat.com/results#!/file/c88e9ff9e59341eba97626d5beab7ebd/regular/information.
The threat name is 'GetCodec.' In this example, the media player was redirected to a link to download a trojan. Seethe scanned trojan here.
Examples of File Type Exploits

Below is a table listing the popular media file formats that have been exploited by routing the user to malicioussites or executing arbitrary codes remotely on target users’ systems.
| File Format | Detection | Description |
| Windows .wma/.wmv | Downloader-UA.b | Exploits flaw in Digital Rights Management |
| Real Media .rmvb | W32/Realor.worm | Infects Real Media files to embed link to malicious sites |
| Real Media .rm/.rmvb | Human crafted | Launches malicious web pages without prompting |
| QucikTime.mov | Human crafted | Launches embedded hyperlinks to pornographic sites |
| Adobe Flash.swf | Exploit-CVE-2007-0071 | Vulnerability in DefineSceneAndFrameLabelData tag |
| Windows.asf | W32/GetCodec.worm | Infects .asf files to embed links to malicious web pages |
| Adobe Flash.swf | Exploit-SWF.c | Vulnerability in AVM2 'new function' opcode |
| QuickTime.mov | Human crafted | Executes arbitrary code on the target user's system |
| Adobe Flash.swf | Exploit-CVE-2010-2885 | Vulnerability in ActionScript Virtual Machine 2 |
| Adobe Flash.swf | Exploit-CVE2010-3654 | Vulnerability in AVM2 MultiName button class |
| Windows .wmv | Exploit CVE-2013-3127 | WMV Video Decoder Remote Code Execution Vulnerability |
| Matroska Video .mkv | Exploit-CVE2019-14438 | Vulnerability in VLC, executes arbitrary code with privileges on the target user's system |
Solutions
Many anti-malware vendors now have added detection by looking for the URL signatures inside media type files. OPSWATMetaDefender Multiscanning technology leverages 35+ anti-malware engines and significantly improves detection ofknown and unknown threats. Deep CDR also supports video and audio file formats and can help to prevent Zero Dayattacks. MetaDefender’s file-based vulnerability assessment technology can detect vulnerabilities in media playerinstallers before they are installed.
If you don’t have OPSWAT Solutions, you need to pay more attention to media files, do not view untrusted files, neverrun media players with elevated privileges, and don't accept downloads of unknown codecs or strange licenses. Alwayskeep your media player software up-to-date to avoid vulnerabilities.
References
[1]National Vulnerability Database.
[2]Killer Music: Hackers Exploit Media Player Vulnerabilities.
[3]David Thiel. 'Exposing Vulnerabilities in Media Software'.
[4]Colleen Lewis, Barret Rhoden, Cynthia Sturton. 'Using Structured Random Data to Precisely FuzzMedia Players'.
For more information, please contact one of our critical infrastructure cybersecurity experts.
Tags:Metadefender Cloud, Deep CDR, File-Based Vulnerability Assessment, Multiscanning- rss
- Academy17
- Advanced Threat Prevention56
- CEO's Blog21
- Company Announcements44
- Cross-Domain Solutions33
- CTO's Blog23
- CVEs199
- Deep CDR42
- Email Security22
- File Upload Security15
- Malware Analysis76
- OACCP Certification32
- OESIS Framework12
- Product Announcements178
- Reports28
- Secure Access23
- Secure Data Storage16
- Technology Partnerships38
- Vulnerabilities21
- File Upload Protection – 10 Best Practices for Preventing Cyber Attacks
- MetaDefender Prevents Emotet - The World’s Most Dangerous Malware
- OPSWAT Expands Global Availability of Critical Infrastructure Protection
- OPSWAT Announces Expansion of Cybersecurity Training Program
- Avoiding storage data leaks and PII regulation noncompliance
- How OPSWAT Can Help Detect and Prevent the VMware WorkSpace ONE Access exploit (CVE-2020-4006)
- Protecting Critical Infrastructure from Advanced Cyberattacks
- MetaDefender Cloud Hash Reputation Database Now Exceeds 40 Billion
- OPSWAT Continues to Expand OESIS Framework with New Partners
- 6 Potential Security Gaps in File Transfer Process for Critical Infrastructure
This website stores cookies on your computer. These cookies are used to improve the usability of this website and provide more personalized experience for you, both on this website and through other websites. To find out more about the cookies we use, see our Cookie Notice Policy.
When you want to install a new app on a Mac, more often than not they will let you download a .dmg file. For a long time, I thought that dmg file is just a special install package, but when working on the post about hiding files on Mac I found out that it is not so simple and I decided to investigate more.
General Information
What DMG stands for?
DMG stands for Disk iMaGe. macOS uses them to package multiple files and folders in one container which can be downloaded over the internet. Think of DMG files as virtual disks, they can be mounted and unmounted like any other drive. They do not have auto-run capabilities.
How to open a DMG file?
Can A Dmg File Have A Virus
To start working with a DMG file it needs to be mounted. To mount the disk image double click on the DMG file. Double click on DMG files invokes DiskImageMounter app which is associated with these files by default. Once the image is mounted a new icon will appear on the Desktop.
Another way to mount DMG files is opening them from the Disk Utility in LaunchPad.
If the image contains an app installer you can see its contents by right-clicking on the app icon and selecting “Show Package Contents”.
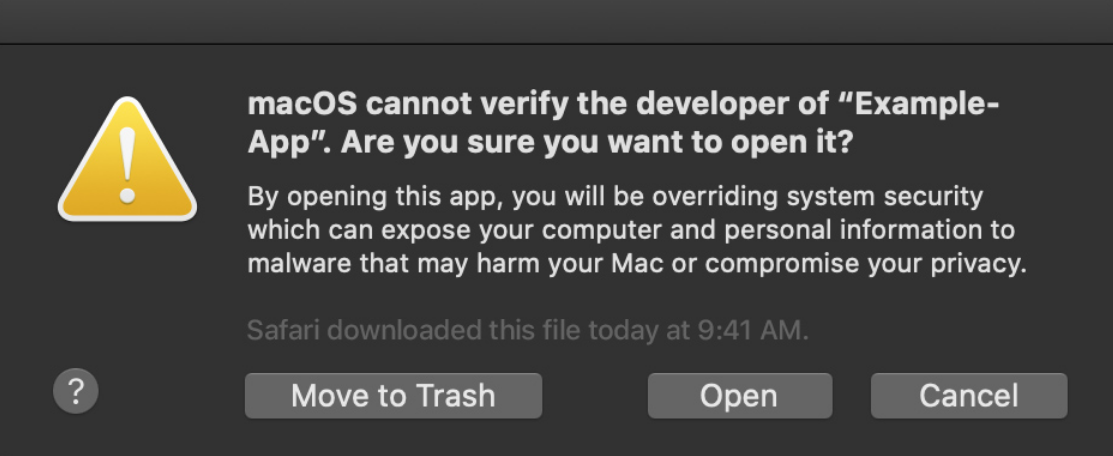
Are DMG files safe to install?
Since DMG file is a disk image its safety depends on its contents. DMG files are neither safe or unsafe, but they may contain viruses or malware inside. When downloading from the internet always make sure that the web site you are downloading is from a trusted developer.

Downloading a DMG file does not compromise Mac security. To understand this better imaging someone packaged a virus in a compressed file, etc. zip file. Viruses get installed only when the container gets executed.
Downloading viruses or malware over the internet on the computer or copying files from one folder to another does not make any harm.
For instance, if you want to download Flash Player or QuickBooks from the internet go to their original web sites: Adobe and Intuit. Do not download software from unknown web sites.
How to check DMG files for a virus?
If you don’t have an antivirus installed on your Mac, you can try the site called Virus Total. The site was developed by a Spanish company, but later it was acquired by Google. It is totally free.
When a file is uploaded to the Virus Total it runs a number of different antivirus applications and prints the results of the scanning.
For instance, when I was working on my article See How Easy Is To Format External Hard Drive For Mac And PC I was able to identify that Minitool DMG contained a malware.
Is there a fake Adobe Flash Player?
I’ve seen many forum posts about fake Flash Players that install malware on Macs. The way they get installed is the web site pops up a warning message “Adobe Flash Player on your computer is outdated” and they provide a link to an updated version or immediately download Flash Player DMG on your Mac.
When this happens, Force Quit the browser and then delete the DMG file from the Downloads folder.
Flash Player (or any other app) will not install if DMG is not mounted and the installer app is not started.
Where do DMG files go?
When downloading DMG files go to the current user Downloads folder by default. However, the browsers may have other folders configured as Downloads, so if the browser didn’t download in the default folder check the browser settings.
If you can’t find the file, learn how to find files here. Just search for files with dmg extension.
When user double clicks on the DMG file the drive mounts and can be accessed either on the Desktop or from a sidebar in the Finder. If the drive is not visible in the Finder go to Finder’s Preferences and enable External disks box under Locations in the Sidebar tab.
Working with DMG files
How to create a DMG file
Anyone who has a Mac can create a DMG file using Disk Utility. With Disk Utility you have options to create a black image or an image from an existing folder. There is a number of things that can be configured for a blank disk image: size, file format, encryption method, partition type, and disk image format.
Let’s review some of the options:
Size: the maximum size of the disk image. Once the disk image is created its size can be changed with Resize option in the Disk Utility.
Format: Use the following rules when deciding which format type to choose:
- If the image will be used both in Mac and Windows choose MS-DOS (FAT) format for images less than 32GB, or ExFAT for images larger than 32GB
- If the macOS version is Sierra or earlier than choose Mac OS Extended
- If the macOS version is High Sierra or later, e.g. Mojave, choose APFS.
There are case-sensitive and case-insensitive options for macOS images. The safest approach is to stick to case-insensitive; they are defaults in macOS. Additionally, some applications may fail when accessing case-sensitive images.
Encryption: 128-bit is recommended, but no encryption provides a faster image.
Partition: Select Single Partition – Guid Partition Map. It is used with Intel-based MacBooks. Apple Partition Map is used with older PowerPC Macs. Master Boot Record Partition Map is used for bootable Windows images.
Image format: If you are not DVD/CD master, then you have a choice between read/write disk image and sparse images. When image format is set read/write then the new image will claim the entire size on disk as soon as it is created.
Sparse images allow creating a small initial image which will expand up to a predefined size. For instance, you can create a 100 MB file and upload only 5MB initially. The size of the image will be 5MB until you add more files. Note, however, the file will not shrink if you delete files. Once expanded it does not contract.
The difference between the sparse image and sparse bundle image is that the former consists of one giant file and bundle consist of a bunch of smaller files. When choosing between two options go with sparse bundle image (the other option is for compatibility with older Mac versions).
It is possible to change either encryption or image format after the image was created. To change encryption or image format start Disk Utility. In the menu go to Images -> Convert. Select the image, change the settings and click Convert.
The Disk Utility will create a new image, it will not override the existing one. So before converting make sure that you have enough storage for both images.
Another way to create an image is from an existing folder. For instance, you may want to create a secret image to store personal files.
Installing apps with DMG files
Since DMG is a container for an app or its installer the process of installing can be one of two following scenarios:
- When DMG file is mounted then it may ask to move the app to the Applications folder. All you need is to drag and drop the icon to the Applications folder icon.
- If the file contains the app installer then double-clicking on the installer will start a wizard which will ask questions and eventually install the app in the Applications folder.
Once the app is installed it is safe to delete the DMG file. In fact, it is recommended to delete unused DMG files to clean the space on Mac. First, unmount it by right-clicking and select Eject from the pop-up menu and then delete the image file.
Can’t delete DMG file?
If any file from DMG file is in use (open with another application) then macOS will not allow deleting the file. Close the application that uses the files from DMG. In case when it is not clear which application is using files from the image restarting Mac will unlock the files.
Additionally, make sure that the disk is unmounted before deleting its DMG file. Sometimes, macOS allows to delete the image file while disk is still mounted, but this is not a good practice.
Why developers use DMGs to install apps on Mac
There are multiple reasons for choosing this format to install the software. Among them are:
- DMG files can be signed. macOS has an option to install software from the App Store only or from the App Store and identified developers. If a developer is a well-known company, e.g. Microsoft, then it gives the user additional assurances that the software came from the developer they trust.
- DMG files cannot be tampered with. So if Microsoft has signed the Skype package it is safe to copy from another computer and install it.
- DMG can be branded with custom icons and background images.
- DMGs can be encrypted.
DMG on Windows
Do DMG files work on Windows?
By default, Windows does not support DMG format. If you want to create an image which can be used between Mac and Windows, then install an application such as 7-zip to open DMG files on Windows.
Note however that 7-zip will only open the image as read-only, you will not be able to add new files or change existing ones.
But make sure that selected configuration for the image file is supported with 7-zip on the Windows you are running. I was able to open an image file with Mac OS Extended and MS-DOS FAT formats, but couldn’t open the one in ExFAT.
There are other options which can extract from DMGs in multiple formats. One of the DMG extractor from reincubate. It’s a paid app, but they do have a free version. Another app is a DMG viewer from Data Forensics which works also with corrupt DMG files.
One thing to remember is that macOS and Windows are different operating systems and applications written for macOS will not work in Windows and the opposite is also true.
So, if you were hoping to install a Mac app on Windows by opening a DMG file on Windows then I have to disappoint you – this won’t work. You can exchange files that are supported on both systems, e.g. .docx or .txt, but binaries are not compatible.
DMG conversion
DMG file to ISO
ISO is another virtual disk image usually used to make a copy of a DVD/CD. It also has to be mounted just like DMG. If you need to convert DMG to ISO format you will need a third-party application.
An example of such application is dmg2iso, it’s free, but it was not maintained for a long time. Another example is AnyToISO – a paid application from Crystal Idea.
Using with VirtualBox
Oracle VirtualBox is virtualization software. The beauty of VirtualBox is that you can run the entire computer inside another computer. For instance, if you need to run Windows on Mac one option is to run a VirtualBox and install Windows OS on VirtualBox instance.
Can Dll File Contain Virus
VirtualBox supports DMG formats as one of the external devices. In order to use DMG with VirtualBox add the image as a virtual optical drive. The image cannot be used a hard drive because it cannot write into it.
Using with VMware
Currently, VMware does not support the DMG format. If you want to use the image with VMware you have to convert it first to ISO.
Conclusion
Can Dmg Files Contain Viruses Windows 10
DMG is not a self-extracting archive which runs and installs software on Mac. It is, however, a container which includes the software to be installed. Disk images by themselves are not dangerous, but they might carry malware inside, so be careful when downloading them over the internet.
Disk images can also be used for personal use, e.g. when you need to package personal files in one container.
Topics: